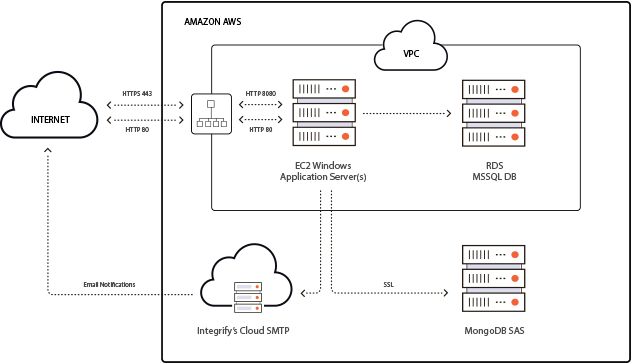
Integrify AWS Private Cloud Infrastructure
Description
All Private Clouds are self-contained within their own VPC or use SSL communication to outside resources for security. We utilize an Amazon Application Load balancer as a firewall device as well as to supply SSL termination. Employing EC2 virtualization for the Application Server allows for the addition of additional nodes to support high availability. Our MongoDB implementation is a SaaS in the Amazon cloud and uses encrypted communication. Microsoft SQL is deployed as an RDS instance for security, speed, and ramp-up flexibility.
Baseline Specifications
Firewall: Amazon Application Load balancer with 443 (HTTPS) to 8080 (HTTP) translation once within the secure VPC space.
Application server: EC2 t3.medium Windows 2016 Server instance with 2 vCPUs and 4 GB RAM. 40 GB system and 100GB Data drives defined. Redis runs on this by default, and all file-based assets (attachments, reports, etc...) are stored here.
MSSQL DB Server: RDS t2.small MSSQL 2017 Web Edition instance with 1 vCPU and 2GB RAM. 100GB is allocated for DB storage. Remote access to customers can be made available vis SSL encrypted connectivity.
MongoDB: Autoscaling MongoDB implementation hosted on AWS through Compose: https://www.compose.com/databases/mongodb
Email Communication: All emails are set to go through our centralized mail server in the cloud by default. This allows for troubleshooting any communication issues with notifications.
Optional: ElastiCache can be implemented within the VPC to offload redis from the application server and additional Application server nodes can be added for increased loads. RDS database can be easily scaled if need be.